Incidents
European CSIRTs report health, energy and transport sectors most targeted in 2024

European CSIRTs report incidents up by 18 percent in 2024 with health, energy and transport sectors most targeted, DDOS continues to impact online services
In July 2016, EU Directive 2016/1148 was adopted with the aim of improving the security of network and information systems across the Union. The NIS Directive prescribed a number of key measures to aid coordination across 27 member states with a strong focus on information sharing.
Under Article 12, national Computer Security Incident Response Teams (CSIRTs) were established to track and respond to threats, risks and incidents impacting operators of essential services in critical sectors and to cooperate across the region.
Member State CSIRTs send annual summaries about their national incident reporting to the NIS Cooperation Group (NIS CG) and an annual report is published showing common incident trends.
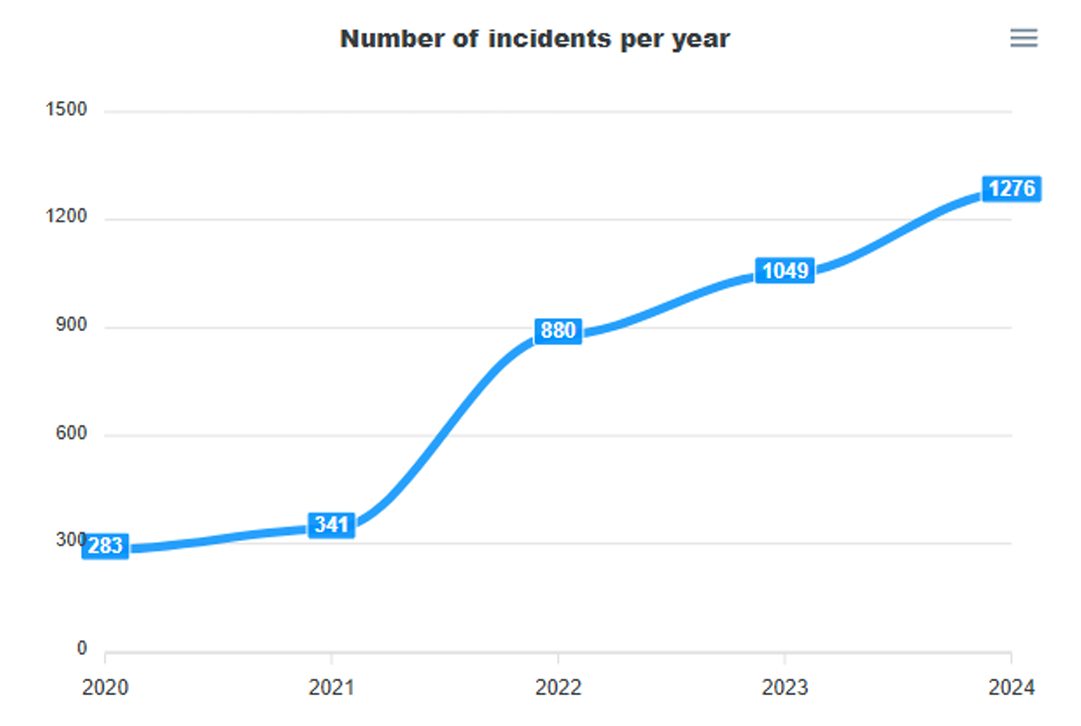
Aggregate reporting data has been published every year since 2020 and the fifth summary report has just been released showing a consistent upward trend in incidents:
Previous NIS Cooperation Group publications including detailed annual incident summaries can be found online.
Key highlights from the 2024 report include:
- The number of reported incidents increased year on year by 18%
- Incidents impacting health, energy and transport sectors accounted for 50% of the total number of reports across those nations reporting data
- Surprisingly, cyber attacks were not the most common cause of harm and disruption - System failures at 51% were the most frequent root cause of reported incidents with most incidents blamed on software bugs, faulty software changes or updates and hardware failures
- Malicious actions - in particular DDoS attacks - caused the most outages and the most lost hours and made up 37% of reported incidents.
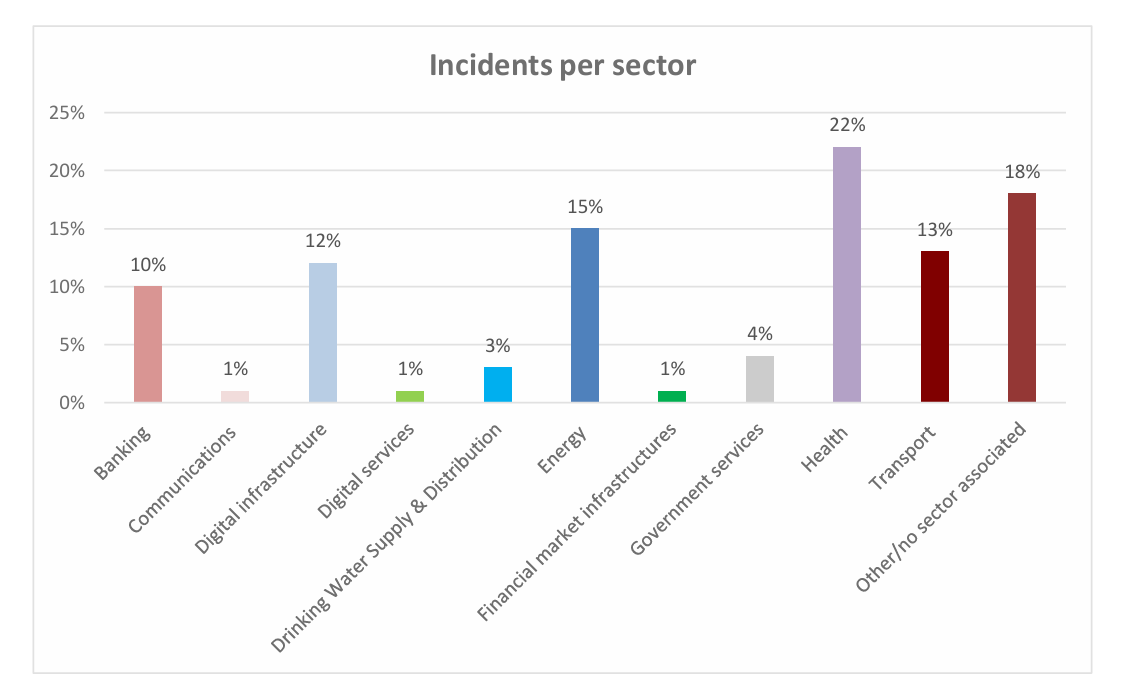
NIS-CG highlighted that cross-border incident reporting remains challenging and that each nation state sets its own criteria and thresholds for reporting cybersecurity incidents affecting operators of essential services with differences also dependent on the sector impacted.
The most common causes of noted incidents were:
- DDoS attacks (9%)
- Software bug (4%)
- Faulty software change/update (4%)
- Ransomware (1%)
- Hardware failure (1%)
With websites and servers the most commonly impacted IT assets.
Classification of incident type and root cause was noted to have significant gaps or variance across the CSIRTs sharing data with 71 % of reports showing underlying technical cause was either not indicated or not known.
With the looming introduction of NIS2, Member States will now submit a summary of incidents on a quarterly basis and ENISA will prepare reports to the CSIRTs network and NIS CG every six months providing faster aggregate analysis of attack trends.
For further information on incident severity splits and detailed analysis across the 7 critical sectors covered by NIS1, visit the Coordination Group website.





.png)

