Frameworks
CISA issues Cybersecurity Performance Goals 2.0 for Critical Infrastructure

The Cybersecurity and Infrastructure Security Agency (CISA) has released updated Cross-Sector Cybersecurity Performance Goals (CPG 2.0) with measurable actions for critical infrastructure owners and operators to achieve a foundational level of cybersecurity.
Originally launched in October 2022 by respected CISA Director Jen Easterly, the original CPGs were promoted as "an approachable common set of IT and OT cybersecurity protections that are clearly defined, straightforward to implement, and aimed at addressing some of the most common and impactful cyber risks" and were designed to be:
- A prioritised subset of cybersecurity practices
- For IT and OT
- Prioritised for risk reduction
- Informed by threats observed by CISA and its government and industry partners
- Applicable across all CI sectors
- Intended to meaningfully reduce risks to both CI operations and to the American people
They were not comprehensive in nature, rather, they were a minimum set of practices that organisations should implement, particularly small and medium Critical Infrastructure, getting organisations started on their path toward a strong cybersecurity posture.
In 2022, they were considered "a floor, not a ceiling" to reduce cyber risk and were very much voluntary in nature compared with sector specific compliance requirements.
As such, there was no link to broader risk management activities and the framework did not include a maturity model for scoring current state - there was however criteria such as “Impact,” “Cost,” and “Complexity” to help organizations to prioritise their investment choices and sequence programmes of work.
The challenges that CPG 2.0 addresses
CISA has updated the guidance to address four main challenges:
- OT cybersecurity often remains overlooked and under-resourced.
The cybersecurity industry continues to focus primarily on business IT systems, frequently neglecting the unique and significant risks posed by OT environments. As more OT devices gain network connectivity, inadequate cybersecurity protections expose critical infrastructure to serious threat. - Many organizations have not adopted fundamental security protections.
The absence of basic protections such as multifactor authentication (MFA), strong password management, and routine backups expose, critical infrastructure to damaging cyber intrusions. - Small- and medium-sized organizations are left behind.
Organisations with limited resources or less mature cybersecurity programs often face challenges determining how to begin implementing reasonable cybersecurity measures and where to invest to try to get the greatest impact to their cybersecurity posture. - Lack of consistent standards and cyber maturity.
There is significant inconsistency in cybersecurity capabilities, investment, and baseline practices across critical infrastructure sectors and this can lead to gaps that threat actors can exploit to cause functional and cascading impacts.
What does the update to CPG 2.0 bring?
Three years on, CISA states that the revised framework incorporates lessons learned, continues to address the most common and impactful threats facing critical infrastructure in 2025 and most importantly, aligns with the updates made to the National Institute of Standards and Technology Cybersecurity Framework 2.0 (NIST CSF 2.0), particularly addressing the key subject of governance.
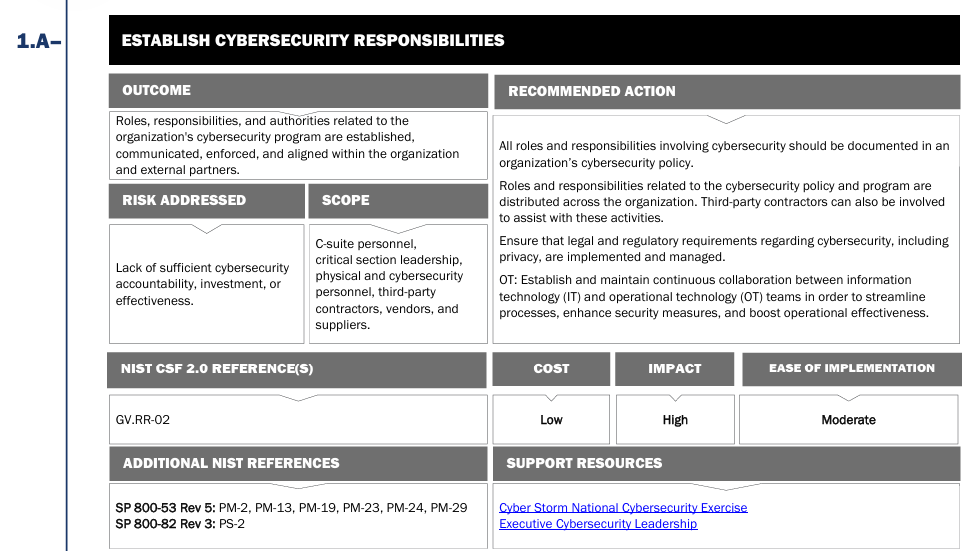
CPG 2.0 now includes the essential role of governance in managing cybersecurity - this includes accountability, risk management, and the strategic integration of cybersecurity activities into day-to-day business operations. It cements the principle that effective governance is the cornerstone of a resilient cyber posture.
The intent remains to provides a baseline set of cybersecurity practices for all CNI operator, prioritised for foundational practices and with guidance for goal-based implementation. The aim after all, is to equip individuals with the means to mitigate risks, benchmark progress, and measure the outcomes.
The highlights include:
- New goals added to address emerging threats and risks including those associated with managed service providers (MSPs), the principle of least privileges, and incident communication procedures.
- CPGs 2.0 removes three duplicate goals based on real-world usage and practitioner feedback.
- Improved Cost, Impact, and Ease of Implementation ratings for each goal with definitions and logic for each rating to help teams decide consistently what will add the 'most bang for the buck'.
A new Cyber Security Evaluation Tool (CSET) and updated CPG 2.0 Checklist will follow in Q1 2026 to enable delivery and measurement.
The revised Cybersecurity Performance Goals 2.0 for Critical Infrastructure sit alongside sector specific guidance, such as the Chemical Sector-Specific Goals (SSGs) and the Information Technology (IT) Sector-Specific Goals (SSGs). Financial Services SSGs will follow next.
For now, review the updated CPG 2.0 guidance, the changelog and controls mapping on the CISA website.







.png)

